TRAINING
Resources to help you expand your skillsetDon’t Fall for It! “Adjustment of Account” Scam
There is nothing scarier than the thought of someone breaking into your business. Unfortunately, this is happening more often than we would like to admit. Business Email Compromise (BEC) is a common scam where the attacker attempts to access company information or money. They do this by posing as a familiar face and requesting sensitive data or financial transactions. It’s vital to be informed about BEC scams and to know the steps you can take to protect your business.
What is Business Email Compromise? BEC is a social engineering attack where a cybercriminal manipulates company employees into divulging sensitive information or performing a financial transaction. The attacker can make their request appear legitimate, such as posing as an executive or a vendor, to make your employees comply. In other cases, attackers hijack an email account to send phishing emails impersonating someone within the company. BEC attacks are often successful because the attacker thoroughly researches your business, making their requests seem authentic.
How can we protect ourselves from BEC scams? The best way to protect your business is to educate your employees about BEC scams. Train them on how to identify potential scams and report any suspicious emails. You can also implement a strict verification process for financial transactions above a certain amount. Be sure to call the person requesting the transaction or use a secondary verification method to confirm the transfer.
Here are some specific steps to take when verifying emails and avoiding phishing:
- Check the sender’s email address. Hover your cursor over the sender’s name to see if it matches the email address provided or if it is a spoofed email address that looks like the real one.
- Look out for grammatical errors or syntax anomalies. These are often tell-tale signs of fake emails. Legitimate companies and individuals likely won’t make basic syntax mistakes in their emails.
- Verify the request. Before sending sensitive information or making a financial transaction, always verify it through another communication channel, such as a phone call or an in-person meeting.
- Never download or click on attachments in suspicious emails. These attachments can be malware or ransomware that can harm your network.
- Implement multi-factor authentication. This security method adds an extra layer of protection by requiring two or more authentication methods to log in.
Business Email Compromise scams are becoming increasingly common and can happen to anyone. The best way to avoid BEC attacks is to educate yourself and your employees, implement strict verification processes, and utilize multi-factor authentication. Protect your business from this cyber threat by being vigilant, well-informed, and proactive. Remember, prevention is always easier than recovery!
How to Use Multiple Desktops in Windows 10
Today, I’d like to demonstrate how to use multiple desktops and Windows 10. Why would you wish to use such a thing?
How to Turn on SharePoint Sync
documents. Now here, you will find an option called saying,
as, as soon as you turn on the sync, it’ll show you this option
and you will click on open Microsoft OneDrive because this
sync will always, uh, be done through the one drives.
How to view two screens at the same time on small screen
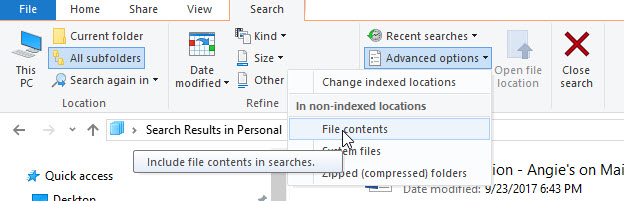
File Search Speed Up Trick
Every try and search for a file in Windows Explorer and have it take forever? There are a few things you can do to speed things up. The first is to stop Explorer from searching the contents of files.
Start by putting your cursor in the search box. This will activate the Search Tools.
Then, select the Advanced Options and un-check the “File Contents” selection.
Switch Office to Touch Friendly Mode
Switch Office to touch friendly mode for use on tablets and touch-enabled devices. Touch mode adds extra space between the Command icons on the Ribbon, making them easier to use.
Must Read for QuickBooks Users!
If you use QuickBooks for your accounting and bookkeeping, then there’s one key thing you must be doing on a regular basis. Failure to do this can result in the loss of data, months’ worth of work, and critical financial information.
At its core, QuickBooks is a database of information. Unless you’re using the Enterprise version, the file that stores the information are what we call a ‘flat file’ database. This means that all your data is stored in a single, proprietary database format file.
The issue is that QuickBooks files are picky. A sudden computer shutdown, multiple users in the same file, and even large files can all lead to corruptio. A corrupted file usually means that you are unable to access your data.
On more than one occasion we’ve had someone come to us in a panic because their QuickBooks file is corrupted. When this happens, you have two avenues of recourse.
First, you can send the file off to Intuit who can repair your file, in most cases. The cost for this is usually around $900.00. Of course, there are no guarantees and this can take them days to complete.
Second, you can restore your file from a backup. You do have a backup correct? However, if you are not using QuickBooks backup feature, then you really do NOT have a backup. What? You say. You don’t need to use QuickBooks’ built-in backup feature because your file is stored on a server that is being backed up?
Yes, I’m here to tell you that is a false sense of security. Your file may very well be getting backed up every day, by whatever method backs up your server. However, all this provides you with is a slightly older version of a file that is probably already corrupted, or may be soon.
You see, the QuickBooks’ built-in backup feature does more than copy your data file from one spot to another. In the background it performs a very important set of checks and maintenance on this file. Each time you run the backup, it performs an integrity check on the file, and does any repairs that might be necessary to prevent data corruption from ever occurring in the first place.
So, no matter what you may be doing to back up your file, our recommendation is that you regularly use the QuickBooks backup feature. It’s perfectly fine to save these backup files on your server, or external drive, if you like. It adds an extra layer of data protection.
You can set QuickBooks to prompt you to run a backup when you close the file. To set this up, run a manual backup.
Use the Options to set the data integrity verification, and how often you want to be prompted to back up your file.
If you need help setting up this type of QuickBooks maintenance plan, we can assist! Call our offices to schedule one of our Solutions Engineers to help you keep your data protected.
7 Critical IT Security Protections Every Business Must Have in Place Now
Securely Share a File with Anyone from OneDrive for Business
You can securely share any file from OneDrive for Business, using your Office 365 account
Did You Know? You can Open a PDF Using Word?
Word 2013 and 2016 will let you convert a PDF to an editable Word document. Then, you can use word to save the document back as a PDF. There are some caveats, and it depends on how the PDF was created in the first place, but give it a try. Check out this Microsoft article for more information
https://support.office.com/en-us/article/Edit-PDF-content-in-Word-b2d1d729-6b79-499a-bcdb-233379c2f63a